Whether during good times or bad times, like a lockdown, security threats are always out there looking for victims. You may have or will soon move to the cloud with Microsoft 365, so you likely need a cybersecurity roadmap and execution plan. We have great news for you! Sherweb has the expertise and staff to help you achieve all your security needs, even for those running on tight budgets and limited resources. But first, let us introduce you to CIS controls and implementation groups so you can take the first step to build a security plan.
Worried you missed a spot in your clients’ security? Take our security assessment and build your offering on the right foundation
Who is CIS and how you can benefit from their work?
The Center for Internet Security® (CIS) is a non-profit crowdsourced global consortium of IT experts that help organizations “identify, develop, validate, promote, and sustain best practice solutions for cyber defense and build and lead communities to enable an environment of trust in cyberspace.”
CIS’s goal is to increase the organization’s visibility of your digital operations, and that includes your physical infrastructure and software applications. With many possible pieces in your infrastructure, smaller organizations may not have the bandwidth to know all entry points. Even small companies can have complex infrastructures, so it is better to know where they are before an attack.
You can find the basic guidelines here broken down in a step-by-step approach. It’s easily digestible for us mere mortals who do not possess PhDs or top-level NSA security clearances.
CIS controls are simple to understand
Upon opening the download, you may feel a bit overwhelmed as you scroll through all of the list’s sub-controls. Don’t worry; the guide is meant to be followed line-by-line so that you can go at your own pace. We recommend that you identify what phase you are in, then plan accordingly.
CIS Phases
- Basic: Network inventory-focused and cost-effective actions. An accounting of all devices and workstations.
- Foundational: A more time-intensive implementation spanning across all organizational operations. Having an expert like Sherweb may be helpful to determine the right areas to focus on.
- Organizational: Typically, a more enterprise-level phase dealing with resource-intensive rollouts that have an ongoing timeline. Again, having an expert like Sherweb may be helpful to determine what to focus on.
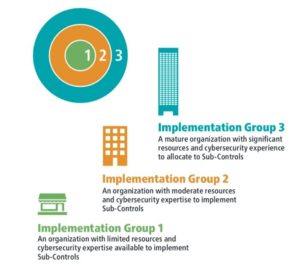
Implementation Groups (IG)
Once you have established your phased approach, you can use CIS Implementation Groups (IGs). IGs are self-assessed categories based on your organization’s relevant cybersecurity attributes. Within each IG, you will find and map which sub-controls are more reasonable to implement depending on your organization’s risk profile and available resources.
The CIS framework breaks the sub-controls into three groups. Implementation groups also continue the simplicity theme. Each group builds upon the previous group as you move up. IG2 builds upon IG1 controls, and IG3 builds upon IG2 controls.
Implementation Group 1:
Aimed at small businesses where data sensitivity requirements are very low, using commercially available off-the-shelf software. These are the core set of sub-controls for organizations with limited resources and expertise. Within IG1, you can identify, define, and plan the execution for future specialized actions or situations.
At Sherweb, we had this group in mind when we created our Office Protect service. Our goal is to simplify security for small businesses that do not have the resources and bandwidth to have dedicated cybersecurity professionals on staff.
Implementation Group 2:
This group is for enterprises that store sensitive business information and have reasonable cybersecurity resources for implementation. IG2 contains more sub-controls for organizations that have dedicated IT teams and higher levels of operational complexity within their hardware and software.
Implementation Group 3:
IG3 operates as a defense against sophisticated adversaries such as Nation State actors utilizing zero-day vulnerabilities. IG3 is for larger organizations that must maintain and coordinate mass amounts of sensitive data and typically have engaged additional cybersecurity experts to assess and execute higher levels of enterprise security.
Help business unit partners roll out
Rolling out a detailed security plan and processes may cause roadblocks in any organization. To avoid pushback, Sherweb has found these steps to be extremely helpful when getting buy-in from business units.
- Communicate your security motivations clearly so business units can see how it benefits them.
- Learn as much as you can about each business unit’s goals, processes, and practices so you can address their concerns first.
- Educate Business Unit leadership on the importance of their role and how they can provide value by notifying staff of possible threats early and often.
Are you looking for easy security management for Microsoft 365? Learn how Office Protect makes security management simple
Sherweb is here for you
CIS Control planning and making needed choices do not have to be painful. If you have questions about the implementation of CIS Controls, Sherweb is here for you. And if you wonder where you stand with your security, be sure to take our security assessment.
Our security products portfolio builds around various levels of controls. We start with Office Protect for the first level and dive deeper with endpoint protection as well as backup and recovery services. On top of this, our NOC and professional services help ensure the safest environment for our partners and their clients.
Let us put our world-class cloud and security architects’ knowledge and experience to work for you!
With Sherweb, you get an expert cloud and security solutions partner that is committed to your success. We offer everything you would need from network operations to architects to professional services to help desk services.
Let Sherweb be your resource to understand how CIS controls and implementation groups would benefit you and your organization.
