This article provides an overview on preparing for ransomware attacks on your Office 365 tenant and the steps to consider if you’re attacked.
What Is Ransomware?
Ransomware is a type of malware or virus that prevents access to devices, files, or applications and demands a ransom payment before you can get everything back. Typically, payment is asked to be made with untraceable Bitcoin on websites that cannot be easily tracked by law enforcement (typically on anonymous networks like the dark web).
The threat, if you do not pay up, is that all of your files will be destroyed. Individuals, businesses, colleges, and government agencies have all been targeted by ransomware.
Simply put: You are a target if you have access to critical files or systems (e.g. Active Directory). And that’s virtually every business.
Learn how Office Protect helps keep your Microsoft 365 tenants safe with our e-book
What Do Ransomware Attacks Look Like?
You’ll know if you’re the victim of a ransomware attack if you:
- Get a pop-up ransomware window that does not close. It may have payment information and include countdown tickers threatening payment increases the longer you delay.
- Cannot open normal files and/or get errors such as a “File is corrupted” or frequent errors stating that your files have the wrong extension.
Here’s an example of a dialog window from the infamous WannaCry ransomware attack in 2017:
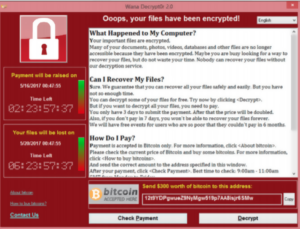
Unfortunately, Ransomware attacks are on the rise, and anyone is a potential victim. Executing security, education, and action plans increases your chances for the best-case scenario—avoiding ransomware attacks in the first place—and helps you mitigate the worst case: saving your data without paying.
How Ransomware Attacks Work
Attackers do their homework in order to target high-value employees via seemingly legitimate email messages. These individuals are often crucial to the organization—think C-level executives and major decision-makers who have access to critical and sensitive documents like financials and customer data lists. High-value staff also includes anyone with mid- or high-level administrator privileges. They may not be up there on the organizational chart, but they do have all the keys to your IT castle. If an attacker lands on them, it won’t be long before they have access to everyone’s password.
Remember: If you have critical files, you are a potential target!
When a user opens an infected email or a malicious attachment, ransomware spreads throughout the network, searching for anything unprotected: desktops, laptops, servers, and mobile devices.
Any user on your Microsoft Office 365 tenant can be vulnerable. Office 365 makes for an efficient attack delivery mechanism. Exchange is linked to everything—just opening an email or saving a spreadsheet can easily advance the threat when either forwarded or placed on SharePoint or OneDrive for mass consumption.
Always use vigilance when opening emails or files from any and all untrustworthy and unknown sources!
Educate Your Staff with Security Awareness Training
While most people are likely aware of Nigerian royalty scams, your staff may not have the knowledge to recognize more sophisticated attacks (e.g., phishing) delivered through legitimate internet traffic. You need to keep users informed on the basics of IT, email, and physical security. Attack types and threat vectors will only continue to adapt and become more sophisticated. Make sure to constantly update your staff on the latest attacks.
The following are a few key points we recommend when creating a security training plan:
- Don’t open emails and/or files in emails from unknown senders.
- Keep an eye out for emails written in a language that is not used by your business.
- Don’t click on links from unknown senders.
- Don’t go to websites that you don’t recognize, and be cautious with the ones you do know.
- Watch for certain executable file types on emails, or block file attachments entirely (e.g., prevent macros from running in Word and Excel files).
- Don’t save important data locally on personal computers. Use SharePoint, OneDrive, or network drives instead.
- Incentivize your staff to report back any and all suspicious emails they see.
Ransomware Security Plan
Attackers have a plan, and so should you. Having a well-prepared prevention plan and regular training exercises will help you either avoid attacks or recover more quickly should you become a victim.
Here are a few points to keep in mind when creating a ransomware security plan:
- Implement security awareness training yesterday.
- Backup data daily
- To the cloud
- Most Office 365 licenses do not include backup plans even though they are in the cloud.
- Sherweb has many options available. Please contact us at **** for more information.
- To local storage devices
- Be sure to remove the external storage device once a backup is complete.
- To the cloud
Remember: If you have a quality backup system in place, you won’t need to pay the ransom.
- Ensure that antivirus software is installed, configured, and up to date across your network.
- Patch any commonly exploited third-party software your organization uses, such as Java, Flash, or Adobe.
- Restrict administrative rights to only those that need it.
- Use whitelisting software that allows only specified sites and applications to be run on company computers.
- Social media policy: Have a policy in place that limits sensitive work-related information being exposed.
- Filter both executable and password-protected files from emails. Make sure your gateway mail scanner blocks these from going through without inspection.
- Filter or block macro-enabled files like the Word version .docm.Macros are a common way to execute code on the victim machine.
- Research all the features already available to you on your Office 365 tenant. Some licensing plans vary on what is offered and what is an add-on service.
If you’ve been targeted by ransomware, you should consider the following:
- Don’t pay
- Making a payment just encourages attackers, and there is no guarantee that you will get what you paid for.
- Call their bluff
- Tell the attacker that you will pay, but that you need time to get the cash. This will give you time to organize.
- Turn off Wi-Fi or Bluetooth.
- Unplug any USB storage devices or external hard drives.
- Find patient zero
- Immediately disconnect from the network.
- Check if the infected machine had access to:
- Shared or unshared drives or folders.
- Network storage of any kind.
- External hard drives.
- USB memory sticks with valuable files.
- Other cloud-based storage besides Office 365 (e.g., DropBox, Google Drive).
- Discover exactly how much of your file infrastructure is compromised or encrypted based on patient zero.
- Contact your local police and the FBI to get your incident reported.
- In the United States, report ransomware threats or events to the White Collar Crime Center https://www.nw3c.org/and contact the FBI.
- In Canada, report attacks on the RECOL website: antifraudcentre-centreantifraude.ca.
- Gather all hacker correspondence so it can be stored and shared with authorities.
- Inform your webhosting provider of the attack (e.g., Sherweb or Microsoft).
- If Microsoft is aware of the attack, it may have detect and removal tools available.
- Delete all infected files, and download clean versions from your backups.
Staying Safe in the World of Ransomware
All businesses and users are potential targets of ransomware attacks. With thorough planning and user education, organizations can prepare themselves to safeguard systems and sensitive data.
The points above are meant to get you and your organization started. Please make sure to research your security plans thoroughly, back up data daily, and implement security awareness training ASAP.
At Sherweb, we’re committed to securing your company’s data as best as possible against ransomware and other attacks. If you have any questions or want to learn more about how we can help you plan, please get in touch.
