Don’t take the bait! Phishing is a method of trying to gather sensitive information using deceptive emails and data. The goal is to trick the recipient into believing that the message is something genuine, then prompt them to submit personal information such as an email address, password or even credit card information.
Think it can’t happen to you? That’s what every phishing victim probably thought—but phishing is a tried and tested type of cyberattack. It’s also getting increasingly sophisticated. In fact, you can purchase entire plug-and-play phishing kits on the dark web. More than 20% of all security breaches involve phishing (Verizon, 2020). It turns out humans, not hardware or software, are the weak link in the fight against scammers! Instead of deploying advanced technology, criminals simply take advantage of our trust and inattention.
Most phishing victims are individuals in small and medium-sized businesses, not large corporations. A typical scam will involve hundreds of dollars rather than millions; in other words, no company is too small to be scammed.
No one’s truly immune, however, not even IT professionals. Yes, we at Sherweb also get suspicious email that are mostly likely phishing attempts. Let’s dissect one of the spoofs we received recently and what makes it smell phishy. Think of it as a quick crash course in arming yourself against future email phishing threats.
Dissecting a suspicious email
Here’s a phishing email example that could land in your inbox:
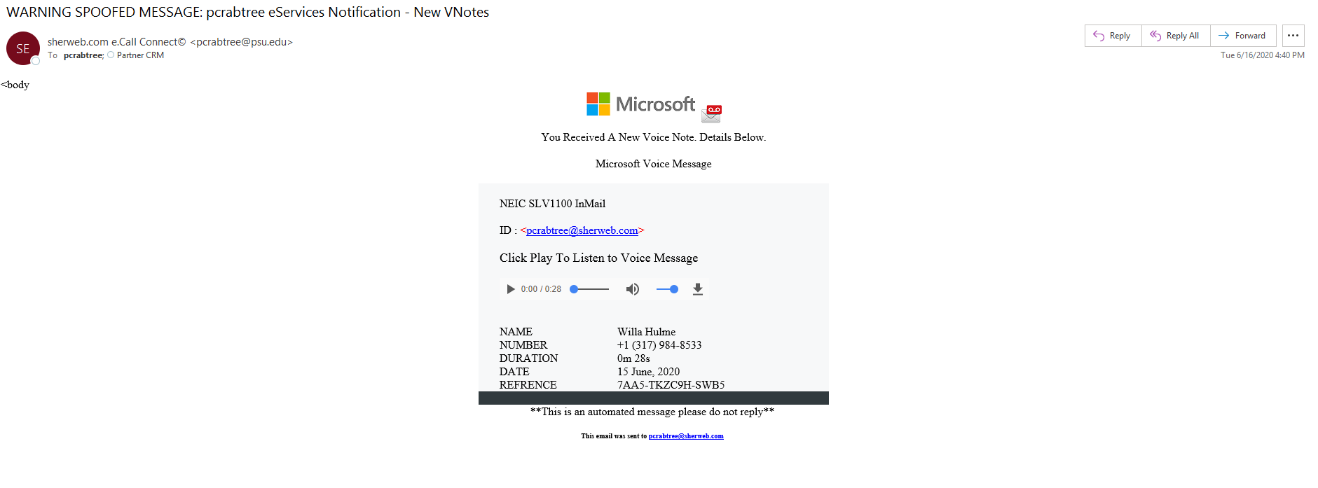
Let’s take a closer look!
Microsoft 365 flagged this message with “WARNING SPOOFED MESSAGE” in the subject line, so the scam is easier to spot from the beginning. Do you always read the subject lines, though? No such warning is present in the body of the message.
Not everyone knows what legit voicemail messages forwarded by Microsoft 365 look like, and it’s surprisingly difficult to validate this against a real-life example online. At first glance, this really does look like a proper voice message; but remember, it’s our lack of attention to detail and tendency to do everything on the fly that the hackers rely on.
Moving on, the somewhat broken HTML in the top part of the message is a red flag. The sender’s name and the university domain the message was supposedly sent from raise concerns as well. What are the actual chances you’d get an email like that out of the blue?
But as with most phishing attempts, the real confirmation is the URL the message is trying to get you to. Here it is below (it’s not clickable, just so there’s no accidents?):
http://t.mail.bose.com/r/?id=h38e3c621,27f0dfd1,27c3bbf1&mc=25_CE_MU_LCB200327
&ad_rid=116318785&ad_blid=954451489&sc=control&p1=analytics.twitter.com/daa/0/daa_optout_actions?action_id=3&participant_id=716&rd=https://cou1sij9sq.s3.us-east-2.amazonaws.com/gooogle.html?&p2=aUmbZ/xcbFqHczTaewMGbjSqTbifnvhiMsVjPAMbRMRoRLyyNIhsCLHX/#pcrabtree@sherweb.com#
Upon inspection, it wants to send you to the website of well-known audio devices manufacturer, Bose. Strange! Of course, the first thing you should be asking is: why would Microsoft send you to a non-affiliated commercial website for you to receive a voicemail? If it looks, dare we say, phishy, you’re better off taking no chances. Always be critical!
The linked webpage is indeed legitimate, in the sense that the sender abuses a flaw in the owner’s website to hide their malicious URL in it. This helps pass the eye test, since the whole scam is less obvious and appears a bit more trustworthy than, say, a message from a Nigerian prince. As the link includes the victim’s email address as a parameter, it can be assumed it will open a page that looks like a Microsoft 365 login, with your username already pre-filled in the login box. Hackers do make things convenient!
If you were to log in and click on the button, it’s game over. Luckily, you now know what red flags to look for along the way, even with spoofs that appear legitimate!
Focus on cybersecurity to combat phishing attempts
This phishing example is just one among countless others. As you can see, cybersecurity is a constant battle. New threats shapeshift at a breakneck speed, while effective classics never really go away. The right security solutions are no longer an optional nice-to-have, but rather an essential part of managing a business.
That includes purpose-built email protection platforms like IRONSCALES, which help MSPs stop phishing and business email compromise before they hit the inbox. It uses AI to flag threats, simulate real-world attacks and automate response across clients.
A strong approach to cybersecurity takes both education and responsive products, and Sherweb can help. We offer a portfolio of hand-picked solutions, so that you can spend less time researching and more time running your business. We also have subject matter experts and learning resources on hand to guide you through security deployment, monitoring and rectifying issues. Contact us or join our partner network today to get started!
